Installing your favourite Linux
If you’ve followed the instructions on page 2 about creating the bootable USB stick you probably already tested some interesting distros for you. Given the install wizards are very straight-forward at this point I’ll cover information about specific installation steps here so you understand a few things that are different compared to Windows when asked for it.
If you did not back up your private data from Windows, do it now!
Then Disconnect the external disk you copied it to to avoid mistakes.
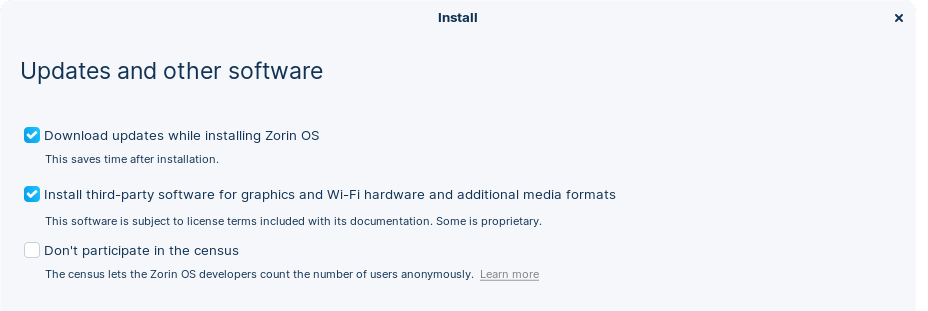
Third-party software for graphics, wifi, media…
During installation you’ll be asked about the installation of third-party software for media formats, drivers and more. You should always make sure to install them unless you absolutely know what you do. While not all of it is open-source you’ll most likely need it either for hardware of specific vendors or playback of media like Netflix or Amazon Prime that use questionable DRM.
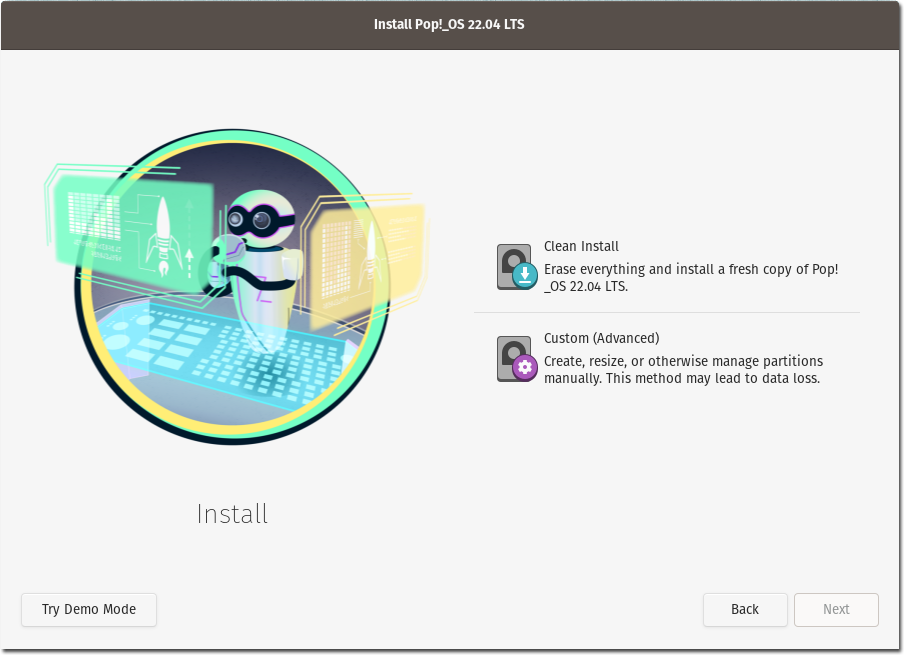
Drive partitioning / Clean Install
Install wizards will ask you if you want to do a clean or “simple” installation or custom. Always choose the easy option here. The advanced custom option expects you to know how a standard Linux operating system needs to be structured which is unnecessary complex for the average user.
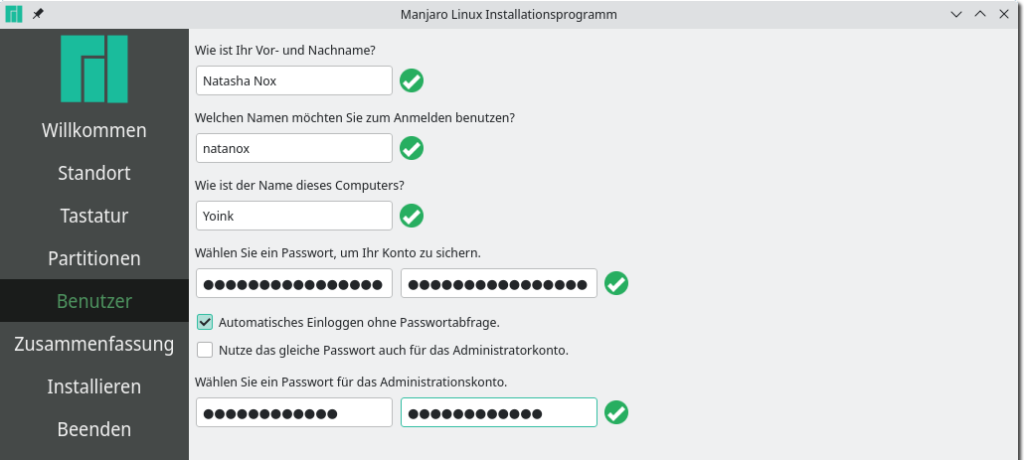
Difference between the Root/Admin and your account password
In addition to your personal account, Linux operating systems do come with an account hidden on the login screen referred to as root, admin or superuser. It has all privileges that exist and is necessary for proper system functionality.
Not all install wizards even ask to set a dedicated password, and for most users it is perfectly fine to use the same password for both your account as well as root. Just make sure to use a safe one.
Trivia: Windows does have a similar concept called “NT Authority”. However they expect their users to be goblins and locked it down.
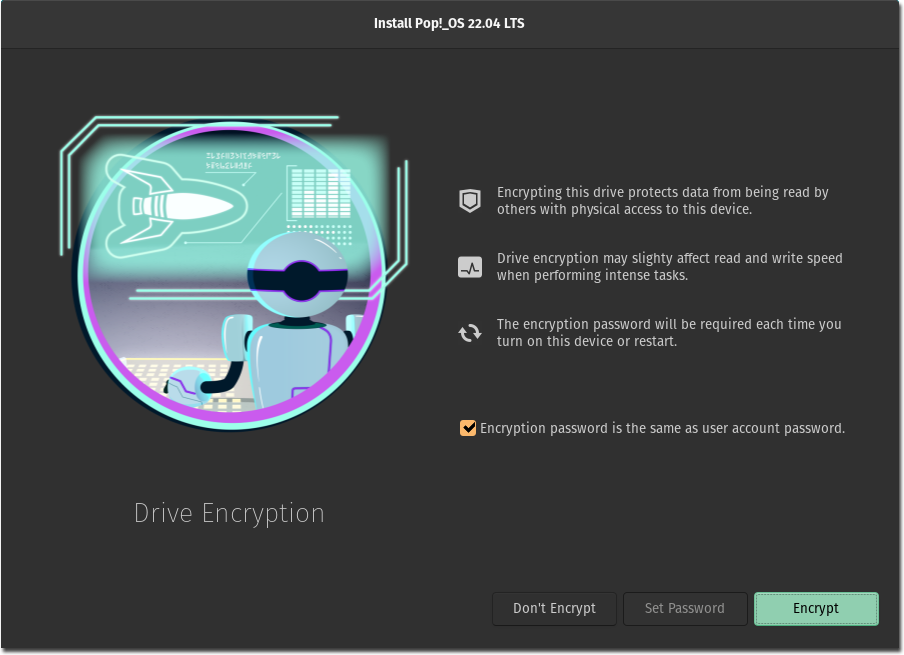
Disk encryption
Some distros will offer you disk encryption during the install process, for example Pop!_OS. Doing so will prompt you during boot to enter your password and make your whole system inaccessible to thieves. However, if you have a high threat model, this is only one part of a bigger process to secure your device and information.
Some distros do not offer it right from the start but only through the custom partitioning settings. I do not recommend trying to set it up by hand unless you’re a professional or ready for a steep learning curve, both LUKS and LVM are highly complex in itself and have to be understood before doing so.

Pingback:Great guide for folks willing to escape to freedom! – Thomas A. Besand
You could add hacktivista.com which is actually only shipping within Chile but is thinking on expanding to latinamerica.